-
Edit -
Attach - Printable
Hard disk hacking (08 Aug 2013)
HTTPS (30 Jul 2013)
- Certificates are required to authenticate communication partners. In other words, make
sure you are really talking to your bank and not to someone who enjoys spending
spare time on building web sites which look surprisingly like your bank's

- Following authentication, a "common secret" is established which is henceforth used to encrypt communication contents. The magic sauce is the Diffie-Hellman-Merkle algorithm. Algorithms like this make it possible to exchange enough information in the open to establish this common secret.
- For performance reasons, subsequent encrypted communication is symmetric.
- Diffie-Hellman key exchange (video)
- Other key exchange algorithms: PSK (pre-shared key), elliptic-curve Diffie-Hellman, RSA, SRP
- What is Diffie-Hellman? (RSA Labs)
- Discrete Logarithm Problem (video)
- Simon Singh: Geheime Botschaften
- https://www.boxcryptor.com
- The First Few Milliseconds of an HTTPS Connection
- https://konklone.com/post/switch-to-https-now-for-free
A subset of Python (30 Jun 2013)
import random import array import sys numbers = array.array('i') flags = array.array('c') solutions = 0 def find_solutions(k, target_sum): global solutions if target_sum == 0: print " Solution:", for i in range(0, len(numbers)): if flags[i] != 0: print numbers[i], print solutions = solutions + 1 else: if k < len(numbers): if (numbers[k] * (len(numbers)-k+1)) >= target_sum: if target_sum >= numbers[k]: flags[k] = 1 find_solutions(k+1, target_sum - numbers[k]) flags[k] = 0 find_solutions(k+1, target_sum) def find_subset_sum(target_sum): global solutions global flags print "Subsets which sum up to %s:" % target_sum flags = [0] * len(numbers) find_solutions(0, target_sum) print "Found", solutions, "different solutions" def subset_sum_test(size): global numbers total = 0 print "Random values:\n ", for i in range(0, size): numbers.append(random.randint(0, 1000)) total = total + numbers[i] print numbers[i], print numbers = sorted(numbers, reverse = True) target_sum = total/2 find_subset_sum(target_sum) subset_sum_test(15 if len(sys.argv) < 2 else int(sys.argv[1]))
Catching up with web frameworks (07 May 2013)
Würdiges Angebot (06 May 2013)
Betreff: Würdiges Angebot von haltbarer Holdinggesellschaft! Sie haben ausgezeichnete verwaltungsmäßige Kenntnisse, ausreichende Fertigkeit im MS-Office. Sie sind aufmerksam, organisiert, repräsentativ, zuverlässig und pünktlich, bewandert im Gebrauch von sozialen Netzwerkseiten wie Twitter und Facebook. Außerdem können Sie gleich in der Belegschaft und unabhängig arbeiten, verstehen und durchführen Sie Erfolgsorientierte Instruktionen, dann suchen wir Sie. Haben Sie Interesse für diesen Job, bitte, senden Sie uns Ihre Kontakt-Information: Voller Name:Hier will jemand auf recht naïve Art Emailadressen sammeln, um sie für Zwecke zu verkaufen, die vom Abseitigen zum Verabscheuungswerten reichen. Nicht weiter der Rede wert eigentlich - abgesehen davon, daß das Deutsch mal wieder so entlarvend spaßig ist, daß man sich fragen muß, wer auf solche Email wohl antworten mag. Die Phishing-Kampagne verwendet als Lockvogel die Begriffe "Würde" und "Haltbarkeit" (Nachhaltigkeit), um den vermeintlichen Arbeitgeber attraktiv zu machen. In diesen unseren Zeiten des Raubritterkapitalismus fast schon ein erfolgversprechendes Rezept, denn genau wegen dieser Begriffe blieb ich an der Nachricht hängen. Liegt aber sicher nur an mir...
Land:
Stadt:
E-Mail:
Bitte bewerben Sie uns per Email für weitere Beschreibung:xxx@yyy.com
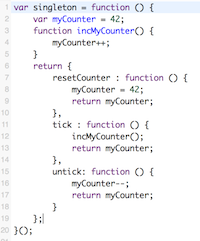
JavaScript: The Good Parts (04 May 2013)
Older topics...
Add a new blog entry.to top
Revisions: | r1.104 | > | r1.103 | > | r1.102 | Total page history | Backlinks
 Blog
Blog